Achieve Service Continuity With Secure Cloud Storage Solutions

Advantages of Secure Cloud Storage
Undoubtedly, secure cloud storage space supplies companies a wide range of benefits in regards to information security and accessibility. Among the primary benefits is boosted safety. By saving data on credible cloud platforms that use security and innovative protection procedures, companies can safeguard their information from unauthorized access or cyber hazards. Furthermore, protected cloud storage space permits smooth scalability, enabling organizations to easily broaden their storage room as needed without the problem of physical upgrades. This scalability is specifically helpful for expanding organizations or those experiencing rising and fall information storage space needs. Additionally, cloud storage promotes reliable collaboration amongst staff member, as it allows for real-time access to shared records and data from anywhere with a web link. This access enhances productivity and simplifies operations by eliminating the restrictions of physical storage space devices or location-dependent gain access to. On the whole, the advantages of safe cloud storage space equate into improved information administration, enhanced functional performance, and enhanced security for services of all dimensions.
Key Functions for Service Connection
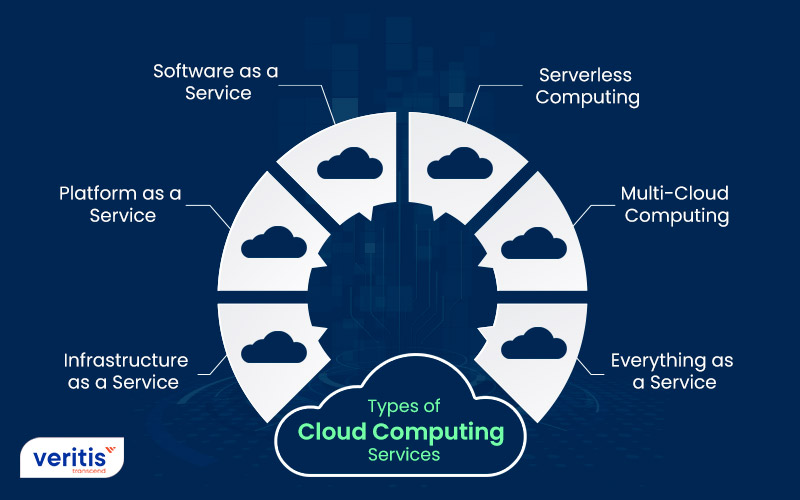
Additionally, an additional crucial function for business connection is redundancy. Redundancy includes having several duplicates of information kept in different areas to stop a single point of failing (universal cloud Service). By dispersing information throughout different web servers or information facilities, services can mitigate the danger of information loss and make certain continuous accessibility to their details. In general, these crucial features collaborate to create an extensive business connection strategy that safeguards critical data and operations.
Relevance of Data Security
In today's interconnected digital landscape, safeguarding sensitive information is extremely important, making the relevance of information file encryption a fundamental facet of preserving data integrity and safety. Data encryption includes encoding details in such a method that just accredited parties can access and decode it. By converting data right into a safe and secure style, file encryption functions as a shield against unauthorized access, minimizing the danger of information breaches and cyber threats.
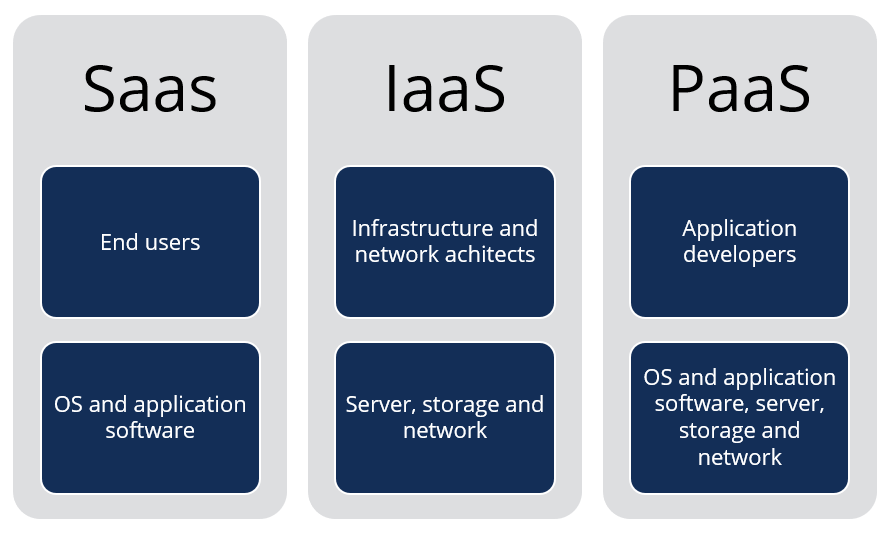
Catastrophe Recuperation Approaches
Effective disaster recovery strategies are necessary for services to make sure and minimize prospective interruptions continuity in the face of unforeseen occasions. A durable catastrophe healing plan entails describing treatments to recover data, applications, and IT infrastructure in case of a calamity. One key facet of an effective technique Find Out More is regular data backups. By keeping information in safe cloud storage space services, services can guarantee that vital info is secured and conveniently obtainable in situation of a catastrophe. Evaluating the disaster healing strategy routinely is also critical to determine any type of weak points and make needed enhancements. Furthermore, having actually an assigned team responsible for implementing the recovery plan can enhance the procedure and reduce downtime. It is important to take into consideration numerous calamity circumstances and customize the recovery methods to address particular risks that business might face. By executing comprehensive disaster recovery approaches, organizations can improve their strength and secure their operations against unforeseen occasions.
Picking the Right Company
To make certain smooth service continuity and efficient catastrophe recuperation, picking a reputable and appropriate service provider for safe and secure cloud storage space is paramount. When selecting a cloud storage space company, numerous key aspects must be considered. Most importantly, review the provider's protection actions. Ensure they use durable file encryption approaches, have rigorous access controls, and abide by sector laws to guard your data. In addition, analyze the supplier's information recovery capacities. A respectable solution company ought to supply normal back-ups, redundancy procedures, and effective healing procedures to lessen downtime in instance of a calamity.
In addition, consider the scalability and flexibility of the cloud storage service. Your business needs may develop in time, so it's vital to pick a copyright that can accommodate your expanding storage space needs and adjust to altering scenarios. Take a look at official source the company's track record and credibility in the industry. Seek testimonials, testimonies, and situation research studies to evaluate their reliability and efficiency. By very carefully examining these elements, you can select a cloud storage space service provider that straightens with your service's requirements and ensures continual procedures in the face of possible interruptions.
Final Thought
Finally, safe cloud storage space services use important advantages for achieving service connection, including improved security functions, smooth scalability, efficient partnership devices, durable data backup devices, and calamity healing approaches. Data file encryption plays an essential function in guarding delicate information, while selecting the ideal solution company is crucial to making certain compliance with policies and preserving functional performance. universal cloud Service. Secure cloud storage is an important possession in today's electronic landscape for making sure uninterrupted business operations
Data backup mechanisms are important for securing versus information loss due to system failings, cyber-attacks, or human errors. By distributing data across different servers or data centers, businesses can reduce the risk of data loss and ensure continuous access to their information.In today's interconnected electronic landscape, guarding delicate info is vital, making the value of data file encryption a fundamental aspect of maintaining information stability and safety. By converting data right into a safe and secure style, file encryption acts as a shield against unauthorized accessibility, lowering the danger of data breaches and cyber hazards.
Conformity demands and data defense guidelines typically mandate the use of security to secure sensitive details, stressing its vital role in modern-day data security approaches.